Module 5: Handling Information - Section 1
Section 1: Security and Storage
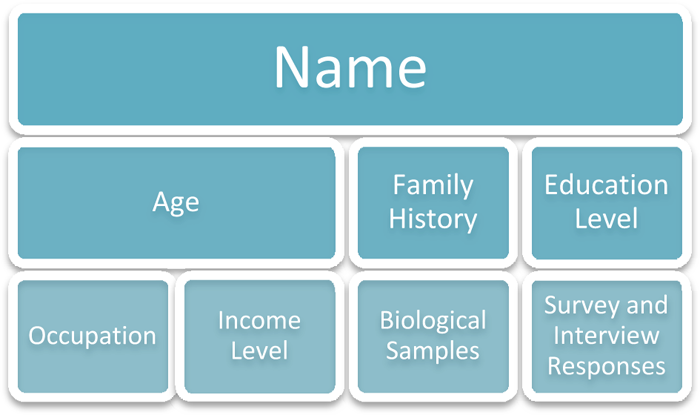 The ethical conduct of research, with human subjects especially, depends in part on protecting the confidentiality of sensitive information such as name, age, occupation, income level, education level, job title, health status, family history, photographic images, survey answers, and interview responses. Even biological samples may reveal information about an individual that could be very sensitive (such as a positive HIV test). Carefully handling information according to the research design will help to ensure that sensitive information collected for research will remain private.
The ethical conduct of research, with human subjects especially, depends in part on protecting the confidentiality of sensitive information such as name, age, occupation, income level, education level, job title, health status, family history, photographic images, survey answers, and interview responses. Even biological samples may reveal information about an individual that could be very sensitive (such as a positive HIV test). Carefully handling information according to the research design will help to ensure that sensitive information collected for research will remain private.
 Research information should always be stored in a secure location. Forms and other study materials that include confidential information (e.g., blood or tissue samples, audio/video-tapes, informed consent forms) should be stored in a locked facility to which only authorized personnel have a key. Computers should be password protected and the user should log-off when the computer is not in use.
Research information should always be stored in a secure location. Forms and other study materials that include confidential information (e.g., blood or tissue samples, audio/video-tapes, informed consent forms) should be stored in a locked facility to which only authorized personnel have a key. Computers should be password protected and the user should log-off when the computer is not in use.
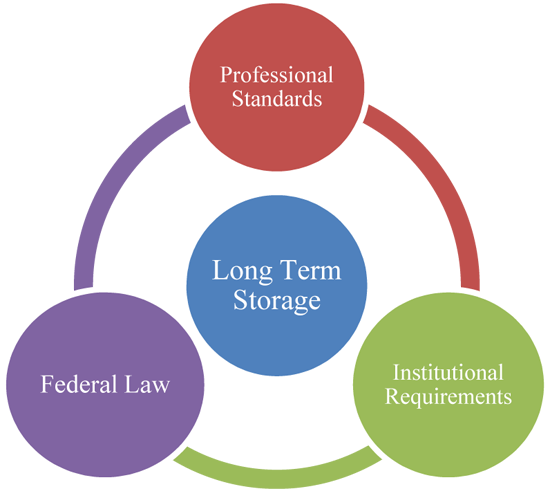 Research information is often stored for several years after the study is completed. This is done for several reasons. First, long term storage may be necessary to comply with professional standards, institutional requirements, or federal law. For example, federal regulations require that informed consent documents be stored for at least three years. Second, researchers may want to keep raw data to prove the accuracy (i.e., validity) and precision (i.e., reliability) of the information they collected during a study. Third, samples or other information such as interview transcripts may be kept for future analyses. When data are kept in a digitized form, there should be at least one additional place where the information is kept in case the original data source is lost or damaged.
Research information is often stored for several years after the study is completed. This is done for several reasons. First, long term storage may be necessary to comply with professional standards, institutional requirements, or federal law. For example, federal regulations require that informed consent documents be stored for at least three years. Second, researchers may want to keep raw data to prove the accuracy (i.e., validity) and precision (i.e., reliability) of the information they collected during a study. Third, samples or other information such as interview transcripts may be kept for future analyses. When data are kept in a digitized form, there should be at least one additional place where the information is kept in case the original data source is lost or damaged.
Definition: Research information should always be stored in a secure location.
Case Example for Security and Storage
In a needs assessment study on helping a clinic reach individuals without health insurance, the study forms included sensitive health information along with the person's name and phone number. Before returning to the research office, the staff member left the information at home on her kitchen counter. That night, some of her friends came over for dinner, saw through the papers, and recognized the names of some of the individuals in the study.





